How to Secure Your Cloud Environment?
Security in any cloud environment is a shared responsibility between the organization and the cloud provider. Here are some actions you can start...
Strengthen your security in the cloud with our AWS Security Blueprint. Implement best practices confidently throughout your cloud journey in AWS.
Navigating the vast array of Best Practices for Security, Identity, and Compliance in AWS can be a daunting task, leaving you uncertain about the most suitable path to effectively secure your workloads within the AWS environment. Nonetheless, these best practices are indispensable for every customer, laying the groundwork to ensure the protection and integrity of data, systems, and assets in the cloud.
The commitment to strengthening your overall security posture is deeply rooted in the strategic design of your target cloud infrastructure, thoughtfully engineered around the six pillars of the AWS Well-Architected Framework. When aligning your cloud strategy with these foundational pillars, you construct a robust and all-encompassing security foundation that permeates every aspect of your AWS ecosystem.
In this blog post, however, we will only focus on the Security pillar as we aim to equip you with actionable insights. This AWS Security Blueprint will also provide you with practical implementation strategies, enabling you to reinforce the security of your cloud infrastructure.
Understanding the AWS Shared Responsibility Model
Foundational Principles of the AWS Security Blueprint
1. Establish a Multi-Account Strategy
2. Enforce the Principle of Least Privilege and Separation of Duties
3. Implement Centralized Identity Management
4. Integrate Security in CI/CD Pipelines
5. Implement Multi-layered Security Defenses in Cloud Infrastructure
6. Protect Data at Rest and Data in Transit
7. Establish a Security Governance Committee
8. Implement Proactive Detection of Security Incidents
Before diving into the specifics of AWS security best practices, it's important to understand the concept of the AWS Shared Responsibility Model. AWS operates on a shared responsibility model, wherein AWS manages the security of the cloud infrastructure, while customers are responsible for securing their data and applications in the cloud. This collaboration ensures a robust security framework and encourages customers to implement best practices to protect their assets effectively.
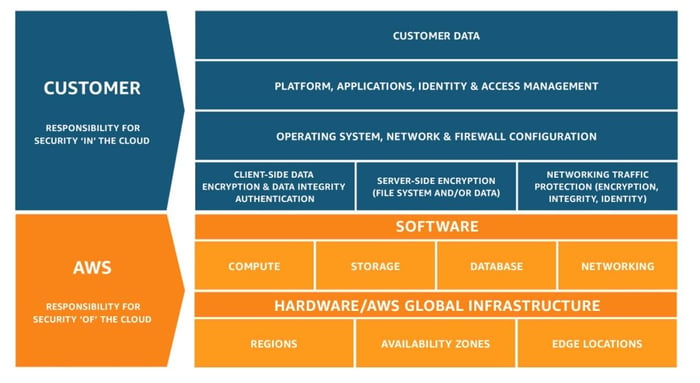 Figure 1: AWS Shared Responsibility Model
Figure 1: AWS Shared Responsibility Model
Within the confines of this model, AWS assumes the responsibility of securing the underlying cloud infrastructure, including critical components like compute, storage, and databases. On the other hand, customers are entrusted with the responsibility of securing their own data, applications, and configurations within the AWS environment. This includes managing user access and permissions, implementing encryption for data at rest and in transit, and configuring firewalls and security groups to control traffic flow.
It is important, however, to emphasize that network security falls under both the AWS and the customer’s purview. To make things clearer, AWS takes charge of securing the physical network infrastructure, while the customer takes charge of securing the virtual network infrastructure. This dual approach ensures a comprehensive security posture that bolsters the entire cloud ecosystem effectively.
By internalizing this model and acknowledging the significance of shared responsibility, organizations can better appreciate the importance of implementing AWS security best practices.
Securing your AWS environment starts with a strong foundation built on proven principles. The AWS Security Blueprint provides a structured approach to protect your data, applications, and workloads while enabling your organization to scale confidently in the cloud.
A multi-account strategy lays the groundwork for a successful AWS adoption journey. Organizing workloads in separate accounts is highly recommended as it provides workload isolation based on function, compliance requirements, or a common set of controls.
Here are some guidelines for creating accounts in AWS:
When setting up the AWS root user account, it is crucial to consider the email address used, as this email will serve as the root user that allows password resets. Use an e-mail address hosted by your corporate domain, preferably a distribution list, to ensure seamless access to the root user even in the event of staff changes.
Deactivate programmatic access to the root user to reduce the risk of exposing the root user credentials.
Avoid generating access keys for the root user. In cases where root user access keys already exist, transition any processes using those keys to utilize temporary access keys from AWS IAM roles, and subsequently, remove the root user access keys permanently. This practice enhances security by minimizing the exposure of long-term access credentials associated with the root account.
If you need credentials for the root user, use a complex password. Turn on multi-factor authentication (MFA) for the root user, further reinforcing the security of the root account and mitigating potential risks associated with unauthorized access.
Limit the use of the root user account when performing tasks in AWS. Restricting the root user's access only to activities that require root user credentials reduces the likelihood of accidental misuse of resources.
AWS Organizations provides a consolidated way to manage multiple AWS accounts. You can group accounts into organizational units (OUs) based on different environments, such as production, development, or test workloads, each with distinct requirements and purposes. This practice enhances account management and facilitates streamlined administration within your AWS environment.
As you run multiple workloads on AWS, robust identity management and permissions are essential to ensure proper resource access. Enforcing the principle of least privilege means that you only grant the users the permissions required for them to perform their tasks.
It is also recommended to enforce the separation of duties where each user has distinct responsibilities. This approach ensures that only authorized users are allowed to perform specific tasks on AWS.
Centralized Identity Management plays a pivotal role in orchestrating access permissions across AWS accounts, enforcing the principle of least privilege, and ensuring that the right users have appropriate access to resources. This approach simplifies the complex task of managing user identities, roles, and access policies.
By consolidating identity management into a centralized system, organizations can establish a unified and standardized access control framework across multiple AWS accounts. This centralization not only fosters efficient management but also ensures consistency and adherence to security policies throughout the organization. Moreover, centralized identity management fosters accountability and transparency by providing detailed audit logs and user activity reports. These logs enable organizations to monitor events, track changes to permissions, and detect potential security anomalies promptly.
Last year, we introduced the Central Syslog Server, facilitating central storage of Syslog messages with integrated search and alerting capabilities. While this feature was initially developed for system messages, its adaptability extends to identity management as well. The versatility of IT-Conductor enables seamless orchestration of various components within an IT environment, making it entirely feasible to leverage this capability for robust identity management purposes.
 Figure 2: Sample Syslog Server Query Results
Figure 2: Sample Syslog Server Query Results
Continuous Integration and Continuous Deployment (CI/CD) pipelines are integral to the development and deployment process of software applications. By designing CI/CD pipelines to test for security issues whenever possible, organizations can proactively identify and address vulnerabilities early in the development lifecycle. This ensures that security is prioritized from the onset and mitigates potential risks in the long run.
Here are some practical steps on how you can implement security checks at various stages of the development and deployment process:
Perform source code scanning to identify potential vulnerabilities. You can also conduct Source Composition Analysis (SCA) to uncover security flaws arising from third-party code or libraries used in the application.
Perform security assessments to run in parallel with performance testing on new application builds before release, enabling early detection of vulnerabilities to injection attacks or insecure configuration settings.
Perform continuous security monitoring and testing after deployment to identify and respond to risks that may emerge in production. This ongoing security assessment, known as runtime security, encompasses scrutinizing infrastructure as code (IaC) templates and evaluating identity access management (IAM) rules for potential security breaches in the application’s hosting environment.
Applying security measures at every layer of the cloud infrastructure is necessary to strengthen your security posture. As part of the shared responsibility model, AWS assumes the responsibility of safeguarding the underlying physical infrastructure, ensuring that stringent security controls are in place. Entry to data center facilities is limited, and only authorized personnel are granted console access to physical devices such as routers, switches, and servers. This reduces the risk of human error and potential misconfigurations.
AWS also ensures that all data traversing its global network, which connects data centers and Regions, is automatically encrypted at the physical layer. This encryption process takes place before the data leaves AWS's highly secure facilities, providing an additional layer of protection to safeguard the information in transit.
There are several security defenses that can be implemented from the customer’s end. To further enhance the protection of your cloud infrastructure, here are some key measures to consider:
Enforce fine-grained security policies across your workloads to secure and protect your applications.
Regularly conduct scans and apply patches to address vulnerabilities in your code, dependencies, and infrastructure. Timely updates and patched known vulnerabilities will reduce the risk of exploitation by malicious actors.
Minimize the utilization of unused components, libraries, and externally consumable services. Reducing the number of active components mitigates the risk of overlooking security gaps or exposing unnecessary points of entry.
Adopt the Zero Trust security model, which treats application components or microservices as independent entities, eliminating trust among them. In this approach, no component or microservice relies on the trustworthiness of others, reinforcing a stringent security posture within the environment.
Design and implement a layered network by logically grouping networking components with similar sensitivity requirements. Grouping resources in layers minimizes the scope of impact in case of unauthorized access. For instance, segregating a database cluster in a virtual private cloud (VPC) with no internet access into subnets without any routes to or from the internet enhances security.
Leverage VPCs to define your network topology, spanning an AWS Region with a private IPv4 address range that you set, or an IPv6 address range selected by AWS. Subnets can be created within a VPC in different Availability Zones, each with an associated route table defining routing rules for managing traffic within the subnet. Internet-routable subnets can be established by adding routes to an internet or NAT gateway attached to the VPC or through another VPC.
Implement security measures at the network edge, which includes web applications and API endpoints, to mitigate the risks of unauthorized access to external-facing components. Learn more about Security at the Edge: Core Principles.
Data protection is of the utmost importance in maintaining a secure and compliant AWS environment. To ensure the highest level of security for your data, it is important to understand its type, classification, storage location, ownership, and associated business processes.
Key data types include:
Intellectual Property (IP), such as trade secrets, patents, and contract agreements
Protected Health Information (PHI), such as medical records that contain medical history information
Personally Identifiable Information (PII) such as name, address, date of birth, and national ID
Credit card data such as primary account number, cardholder name, expiration date, service code number
Once you know the classification level of the data you’re handling, you can utilize resource tags to separate AWS accounts per sensitivity. When making authorization decisions based on tags, ensure that the permissions associated with the tags are appropriately defined using tag policies within AWS Organizations. This practice guarantees that access controls align with your organizational requirements, reinforcing a robust and well-structured security framework.
Data at rest refers to information residing in non-volatile storage within your workload, such as block storage, databases, and archives. To protect data at rest, employ encryption and tokenization techniques. These measures render unintelligible data to unauthorized users, even if breaches occur. Moreover, enforce access control mechanisms like isolation and versioning to fortify data protection further.
Data in transit refers to information transmitted from one system to another. Implementing secure protocols, such as Transport Layer Security (TLS) or IPsec, provides authentication and confidentiality during data transmission. These protocols significantly reduce the risk of data tampering or loss during transit, ensuring data integrity. To further strengthen data security, enforce encryption requirements when transmitting sensitive data outside your Virtual Private Cloud (VPC). This precautionary step mitigates the risk of data interception by unauthorized entities and ensures the confidentiality of critical information.
Enhancing cloud security by enforcing standardized policies, procedures, and best practices across an organization can be achieved by establishing a security governance committee. Taking an organizational approach to governance empowers teams to operate securely in the cloud environment, ensuring consistent compliance with organizational, legal, and industry-specific requirements.
Here are some key responsibilities of the security governance committee:
Identify compliance requirements relevant to your workload. By identifying and aligning with these requirements, organizations can tailor security measures to meet specific industry standards and regulatory guidelines.
Keep updated with security threats and recommendations. Regularly monitoring security advisories, updates, and best practices helps organizations respond promptly to emerging threats, minimizing the potential impact of security incidents.
Manage the utilization of common capabilities and shared components instead of having individual workload owners invest in security specific to their workloads. This approach fosters collaboration and standardization, enabling teams to utilize services like AWS account creation, centralized identity management for personnel, and common logging configurations. By leveraging shared components, workload cycle times improve, and security control, objectives are consistently met.
Effective detection capabilities are essential for proactively identifying security incidents and potential threats within your AWS environment. By promptly detecting security incidents and potential threats, organizations can swiftly respond and mitigate risks, thereby improving the overall resilience of the AWS environment.
To support the proactive detection of security incidents, you can also perform the following:
Implement checks in CI/CD pipelines or source control to allow the verification of configurations before deploying workloads. This proactive approach ensures that unwanted configurations are caught early in the development process, minimizing the risk of deploying insecure or non-compliant resources.
Enable real-time alerting mechanisms to promptly notify security teams when unexpected or potentially malicious activities occur within your AWS accounts. By receiving immediate alerts, organizations can swiftly investigate and respond to security incidents, preventing potential damage.
Monitor mutating API calls that deviate from expected patterns to proactively identify suspicious activities such as unauthorized modifications or security breaches.
Monitor and collect logs and metrics from AWS services and applications to provide crucial traceability for your AWS environment. Utilizing a centralized syslog monitoring system enables efficient log management and analysis. Earlier this year, we also introduced a new feature to integrate alert notifications with collaboration tools such as Microsoft and Slack. Learn more about it here.
Integrate security events and findings into notification and workflow systems, such as ticketing systems, bug trackers, or Security Information and Event Management (SIEM) platforms. This approach streamlines incident response and enhances security operations.
A comprehensive incident response plan documents the step-by-step actions to be taken when security incidents occur. It defines roles, responsibilities, and communication protocols, ensuring a coordinated and effective response to incidents.
The incident response process should be continuously evaluated and improved to enhance its effectiveness. Regular assessments help identify security gaps and weaknesses, enabling organizations to address and remediate potential vulnerabilities promptly.
A proactive approach to incident response involves preparation, simulation, and iterative improvement. Regularly conducting simulated incident scenarios enables security teams to practice their response procedures, identify weaknesses, and refine their incident-handling capabilities.
Standardizing the incident management process across the organization enhances response efficiency and consistency. Implementing well-defined incident response procedures allows for rapid detection, investigation, and recovery from security incidents.
The AWS Security Blueprint serves as a comprehensive guide for organizations seeking to fortify cloud protection measures. By adhering to multi-layered security strategies, adopting a Zero Trust model, and implementing robust identity management, organizations can create a secure foundation in AWS.
The blueprint emphasizes the significance of continuous monitoring, efficient incident response, and data protection to safeguard valuable assets and maintain compliance with regulatory requirements. Embracing these best practices and recognizing AWS's shared responsibility model empowers organizations to navigate the cloud landscape confidently, fostering a culture of trust and resilience among stakeholders.
As cyber threats continue to evolve, the AWS Security Blueprint remains an indispensable resource in the pursuit of optimal cloud security and a steadfast commitment to safeguarding data, systems, and assets within the AWS environment.
Even with a strong commitment to security, organizations can make mistakes that leave their AWS environments vulnerable. Some common pitfalls include: Over-reliance on default settings, excessive permissions, neglecting multi-account strategies, skipping encryption or key management, inadequate monitoring and logging, ignoring CI/CD security integration, weak incident response planning, and overlooking shared responsibility nuances.
Monitoring the right metrics and KPIs helps ensure your AWS security practices are working effectively and enables proactive risk management. Key metrics include: number of security incidents or breaches, mean time to detect (MTTD) and mean time to respond (MTTR), compliance posture, configuration compliance, and more.
Network security in AWS differs from on-premises primarily due to its virtualized, automated, and shared-responsibility nature. In AWS, the cloud provider secures the physical infrastructure, while customers focus on securing virtual networks, such as VPCs, subnets, and security groups. Network segmentation, access control, and monitoring are largely implemented through software-defined controls and cloud-native tools like GuardDuty, Security Hub, and CloudTrail, enabling dynamic and automated protection that adapts to scaling workloads.
In contrast, on-premises network security relies more on physical infrastructure and manual processes. Segmentation is often achieved through VLANs and firewalls, monitoring depends on SIEM tools or manual log collection, and access control may require separate systems. Overall, AWS emphasizes automation, fine-grained identity integration, and elastic protection, while on-premises environments focus on static, hardware-based security controls.
Organizations can prepare for AWS security audits by understanding applicable regulations (e.g., ISO 27001, HIPAA, PCI DSS), implementing standardized policies for access, encryption, logging, and network configurations, and leveraging AWS tools like Config, Security Hub, and CloudTrail to monitor compliance and generate audit-ready reports. Maintaining clear documentation, performing internal audits, and training teams ensures consistent application of security controls, making audits smoother and helping demonstrate a strong, compliant security posture.
Security in any cloud environment is a shared responsibility between the organization and the cloud provider. Here are some actions you can start...
SAP has launched a Security Patch day, scheduled for the second Tuesday of every month. Here is an updated list of Security Notes through August 2020.
Learn how to assess cloud readiness, optimize costs, enhance security, and ensure seamless cloud migration with IT-Conductor’s expert tools